__FILE__ constant to determine the absolute path of the current script:
<?php echo __FILE__ ; #Prints: D:\xampp\htdocs\example.php
__DIR__ constant to determine the absolute directory path of the current script:
<?php echo __DIR__ ; #Prints: D:\xampp\htdocs
DIRECTORY_SEPARATOR:
To use a path taking into consideration the directory separator character, which is / on UNIX/Linux, \ on Windows, and : on Mac OS X. Usually, / works fine on most systems, but you should note the requirements of the system on which you want to host your site.
It is recommended to use the DIRECTORY_SEPARATOR constant which represents the current OS directory (path) separator:
<?php echo __DIR__ . DIRECTORY_SEPARATOR . 'img.jpg'; # On my Windows OS: D:\xampp\htdocs\img.jpg # On Unixed based OS: /usr/local/htdocs/img.jpg
Using basename() function to retrieve the filename (base name) of the given path:
<?php
//Get the filename portion of a path
echo basename('/var/myfiles/today.txt');
#Prints: today.txt
echo basename(__FILE__);
//Prints: example.php
https://php.net/manual/function.basename.php
Using dirname() function to get the given file’s path:
<?php
//Get path of a file
echo dirname('/etc/path/file.txt') . '<br>';
#Prints /etc/path
echo dirname('css/404.css') . '<br>';
//Prints: css
echo dirname('abc.txt') . '<br>';
# Prints: .
https://php.net/manual/function.dirname.php
Using realpath() function to resolve paths to canonicalized absolute pathnames:
<?php
echo realpath('.') . '<br>';
# D:\xampp\htdocs
echo realpath('abc.txt') . '<br>';
# D:\xampp\htdocs\abc.txt
echo realpath('../img/bitnami.ico');
# D:\xampp\img\bitnami.ico
https://php.net/manual/function.realpath.php
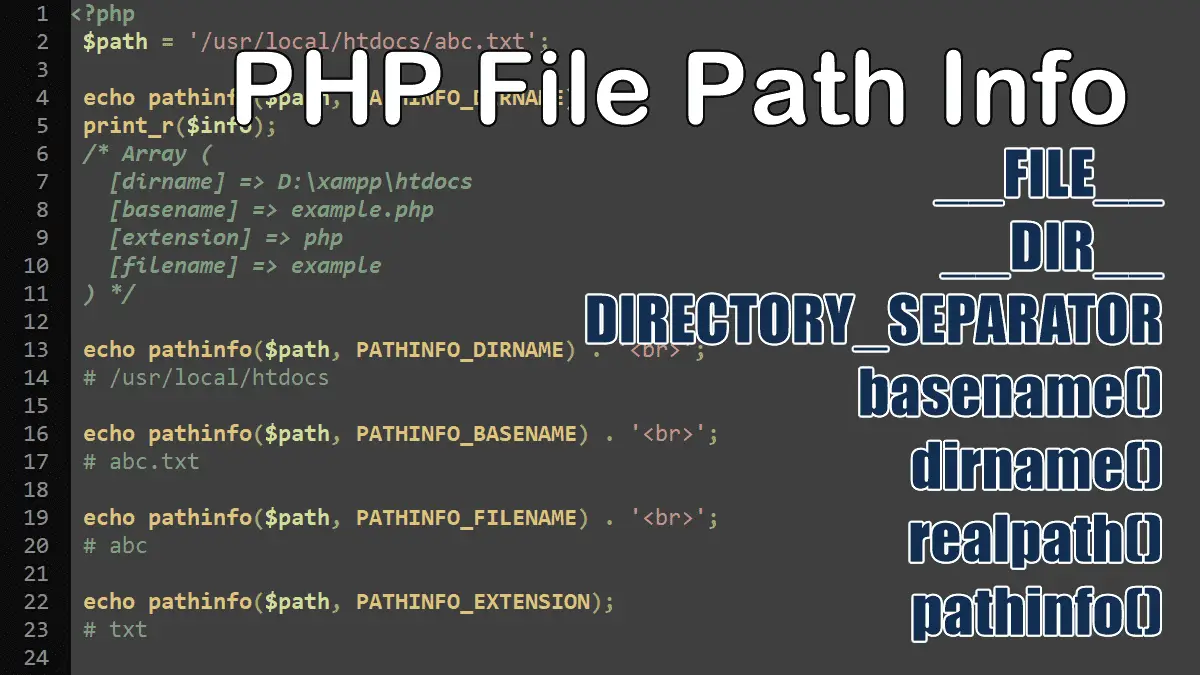
Using pathinfo() function to get information about a file path:
<?php $info = pathinfo(__FILE__); echo $info['dirname'] . '<br>'; # D:\xampp\htdocs echo $info['basename'] . '<br>'; # example.php echo $info['extension'] . '<br>'; # php echo $info['filename']; # example https://php.net/manual/function.pathinfo.php
How to get the file extension with pathinfo()?
The pathinfo($path, PATHINFO_EXTENSION) returns the file extension:
<?php $path = 'images/dog.jpg'; echo pathinfo($path, PATHINFO_EXTENSION); # jpg
The pathinfo() function takes two parameters, the first parameter is the filename and the second argument is a constant that tells the function to return only the specific part of the path. This function accepts the following constants as the second parameter:
- PATHINFO_DIRNAME
- PATHINFO_BASENAME
- PATHINFO_EXTENSION
- PATHINFO_FILENAME
<?php $path = '/usr/local/htdocs/abc.txt'; echo pathinfo($path, PATHINFO_DIRNAME) . '<br>'; # /usr/local/htdocs echo pathinfo($path, PATHINFO_BASENAME) . '<br>'; # abc.txt echo pathinfo($path, PATHINFO_FILENAME) . '<br>'; # abc echo pathinfo($path, PATHINFO_EXTENSION); # txt
Securing File Access
If you are using files with PHP, avoid retrieving the filename from external sources, such as user input or cookies. This might allow users to inject dangerous code into your website or force you to load files you did not want to open.
Some coders had a self-programmed content management system that created uniform resource locators (URLs) like this: index.php?page=subpage.html. This just loaded the page subpage.html into some page template and sent this to the browser. But what if the following URL is called: index.php?page=../../../etc/passwd? With some luck (or bad luck, depending on your point of view), the contents of the file /etc/passwd are printed out in the browser.
This kind of attack called directory traversal attack is quite common on the Web. However, you can avoid becoming a victim in several ways:
- If possible, do not use dynamic data in filenames.
- If you have to use dynamic data in filenames, use
basename()to determine the actual name of the file, omitting the path information. - Set the
php.inidirectiveopen_basedir. This expects a list of directories where PHP may access files. PHP checks the basedir rules whenever a file is opened, and refuses to do so if it isn’t in the appropriate path. - Set
include_pathto a directory you put all to-be-used files into and set the third parameter tofopen()toTrue, using theinclude_path.
Working with Files in PHP:
- Returning or Downloading Files with an HTTP Request
- Reading a File into a String or Array
- PHP Opening and Closing Files
- Reading files by line or by character
- Writing and appending to files
- Reading and Writing CSV Files
- Parsing INI Files and Strings
- Check File Type (whether a file is a directory or a file)
- Understanding file Permissions in PHP
- Reading Information About Files in PHP
- Copying, Moving and Deleting Files in PHP
- Reading Directories Contents in PHP
- Browse directories recursively
- Zipping and Unzipping a File with Zlib and Bzip2
- Zip and Unzip Archives with ZipArchive
- Using Relative Paths for File Access